Cisco IOS Private VLANs
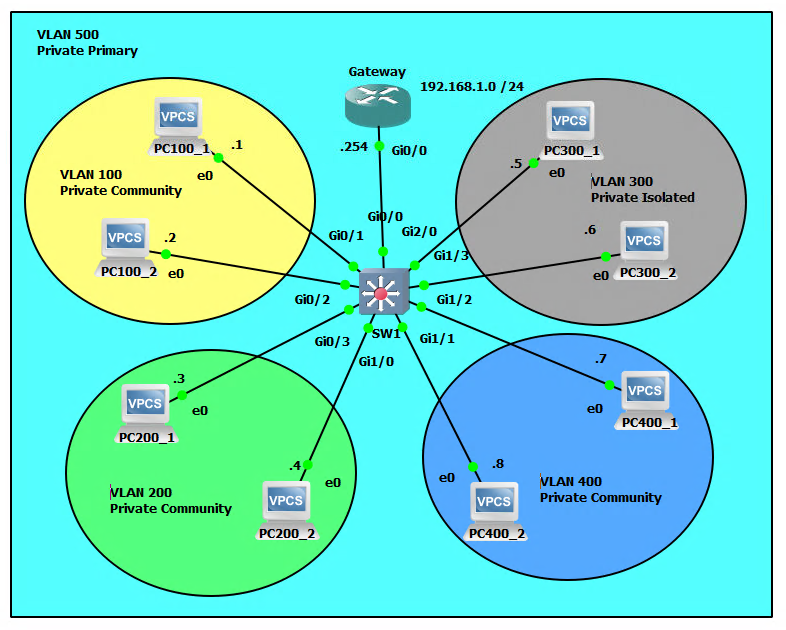
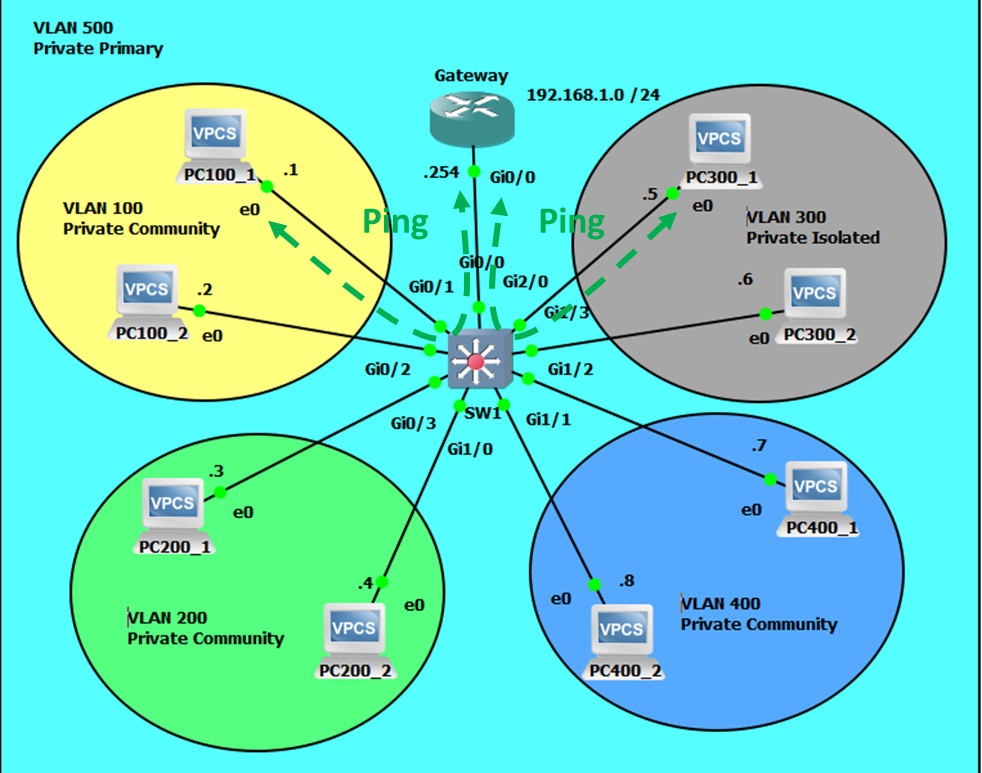
Network Topology
What is a Private VLAN?
A private VLAN, also known as a private LAN, is a VLAN (Virtual Local Area Network) that is used to segment a larger network into smaller, more secure subnets. It is used to isolate different types of traffic or to separate sensitive or confidential information from other network traffic.
A private VLAN typically consists of three types of ports: promiscuous ports, host ports, and community ports. Promiscuous ports can communicate with all other ports in the private VLAN, while host ports can only communicate with promiscuous ports. Community ports can only communicate with other ports in the same community. This allows for a high level of granularity in terms of controlling access and isolating different types of traffic on a network.
Promiscuous ports, isolated ports, and community ports are different types of ports that are used in private VLAN (PVLAN) environments to control access and isolate different types of traffic on a network.
- Promiscuous Ports: These ports can communicate with all other ports in the private VLAN, including host and community ports. They are typically used for gateway or router connections and can be used to access shared resources or provide access to other networks.
- Isolated Ports: These ports can only communicate with the associated promiscuous port and cannot communicate with other isolated or community ports. They are typically used to isolate sensitive or confidential information and prevent it from being accessed by other parts of the network.
- Community Ports: These ports can only communicate with other ports within the same community and not with other communities or promiscuous ports. They are used to create isolated groups within a private VLAN and to control access to shared resources.
In summary, promiscuous ports allow communication with all other ports in the PVLAN, isolated ports are used to isolate sensitive information and prevent it from being accessed by other parts of the network, and community ports are used to create isolated groups within a PVLAN and control access to shared resources.
Private VLANs are often used in enterprise networks, data centers, and service provider environments to segment traffic and provide additional security. They can also be used to isolate guest or IoT traffic, to separate different departments or groups within an organization, or to separate different types of traffic on a network.
What is a Private Isolated VLAN?
A private isolated VLAN is a good solution for keeping sensitive or confidential information separate from other network traffic. It can be used for segmenting a network into secure and non-secure zones, for example, to isolate traffic from a secure server or database from the rest of the network. Additionally, it can be used to create secure zones for specific departments or groups within an organization, or to separate different types of traffic on a network, such as guest or IoT traffic. Some things that Private VLANs can be beneficial for include:
- Segmenting a network into secure and non-secure zones: In this scenario, a private isolated VLAN would be used to separate sensitive or confidential information from other network traffic. This could include separating a secure server or database from the rest of the network, or isolating traffic from a specific department or group that handles sensitive information.
- Isolating guest traffic: In a scenario where guest wireless access is provided, a private isolated VLAN could be used to separate guest traffic from internal network traffic. This would help to prevent guests from accessing sensitive or confidential information on the internal network.
- Isolating IoT traffic: In a scenario where there are a large number of IoT devices connected to a network, a private isolated VLAN could be used to separate IoT traffic from other network traffic. This would help to prevent IoT devices from accessing sensitive or confidential information on the network and also prevent any potential security risks from these devices.
- Isolating different types of traffic: In a scenario where there are multiple types of traffic on a network, such as voice and data traffic, a private isolated VLAN could be used to separate the different types of traffic. This would help to ensure that voice traffic, for example, is prioritized over data traffic, and that there is no interference between the different types of traffic on the network.
Configuration
PCs
PC100_1>ip 192.168.1.1/24 192.168.1.254
PC100_2>ip 192.168.1.2/24 192.168.1.254
PC200_1>ip 192.168.1.3/24 192.168.1.254
PC200_2>ip 192.168.1.4/24 192.168.1.254
PC300_1>ip 192.168.1.5/24 192.168.1.254
PC300_2>ip 192.168.1.6/24 192.168.1.254
PC400_1>ip 192.168.1.7/24 192.168.1.254
PC400_2>ip 192.168.1.8/24 192.168.1.254
Gateway
Gateway>enable
Gateway#configure terminal
Gateway(config)#interface gigabitEthernet 0/0
Gateway((config-if)#ip address 192.168.1.254 255.255.255.0
Gateway(config-if)#no shutdown
SW1
SW1>enable
SW1#configure terminal
SW1(config)#vtp mode transparent
SW1(config)#vlan 100
SW1(config-vlan)#private-vlan community
SW1(config-vlan)#exit
SW1(config)#vlan 200
SW1(config-vlan)#private-vlan community
SW1(config-vlan)#exit
SW1(config)#vlan 300
SW1(config-vlan)#private-vlan isolated
SW1(config-vlan)#exit
SW1(config)#vlan 400
SW1(config-vlan)#private-vlan community
SW1(config-vlan)#exit
SW1(config)#vlan 500
SW1(config-vlan)#private-vlan primary
SW1(config-vlan)#private-vlan association 100,200,300,400
SW1(config-vlan)#exit
SW1(config)#interface gigabitEthernet g0/1
SW1(config-if)#switchport mode private-vlan host
SW1(config-if)#switchport private-vlan host-association 500 100
SW1(config)#interface gigabitEthernet g0/2
SW1(config-if)#switchport mode private-vlan host
SW1(config-if)#switchport private-vlan host-association 500 100
SW1(config)#interface gigabitEthernet g0/3
SW1(config-if)#switchport mode private-vlan host
SW1(config-if)#switchport private-vlan host-association 500 200
SW1(config)#interface gigabitEthernet g1/0
SW1(config-if)#switchport mode private-vlan host
SW1(config-if)#switchport private-vlan host-association 500 200
SW1(config)#interface gigabitEthernet g2/0
SW1(config-if)#switchport mode private-vlan host
SW1(confi-if)#switchport private-vlan host-association 500 300
SW1(config)#interface gigabitEthernet g1/3
SW1(config-if)#switchport mode private-vlan host
SW1(confi-if)#switchport private-vlan host-association 500 300
SW1(config)#interface gigabitEthernet g1/2
SW1(config-if)#switchport mode private-vlan host
SW1(confi-if)#switchport private-vlan host-association 500 400
SW1(config)#interface gigabitEthernet g1/1
SW1(config-if)#switchport mode private-vlan host
SW1(confi-if)#switchport private-vlan host-association 500 400
SW1(config)#interface gigabitEthernet g0/0
SW1(config-if)#switchport mode private-vlan promiscuous
SW1(confi-if)#switchport private-vlan mapping 500 100,200,300,400
SW1(confi-if)#end
Illustrated Scenarios
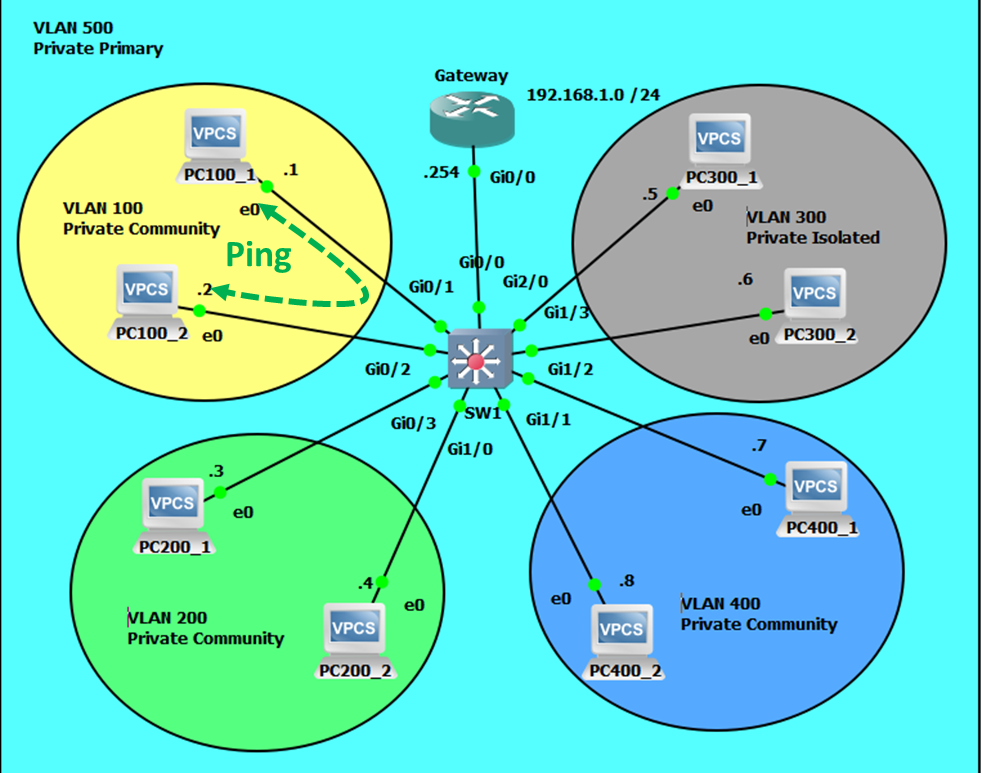
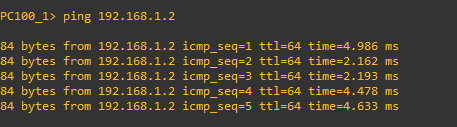
Intra-community VLAN Communication will be Successful.
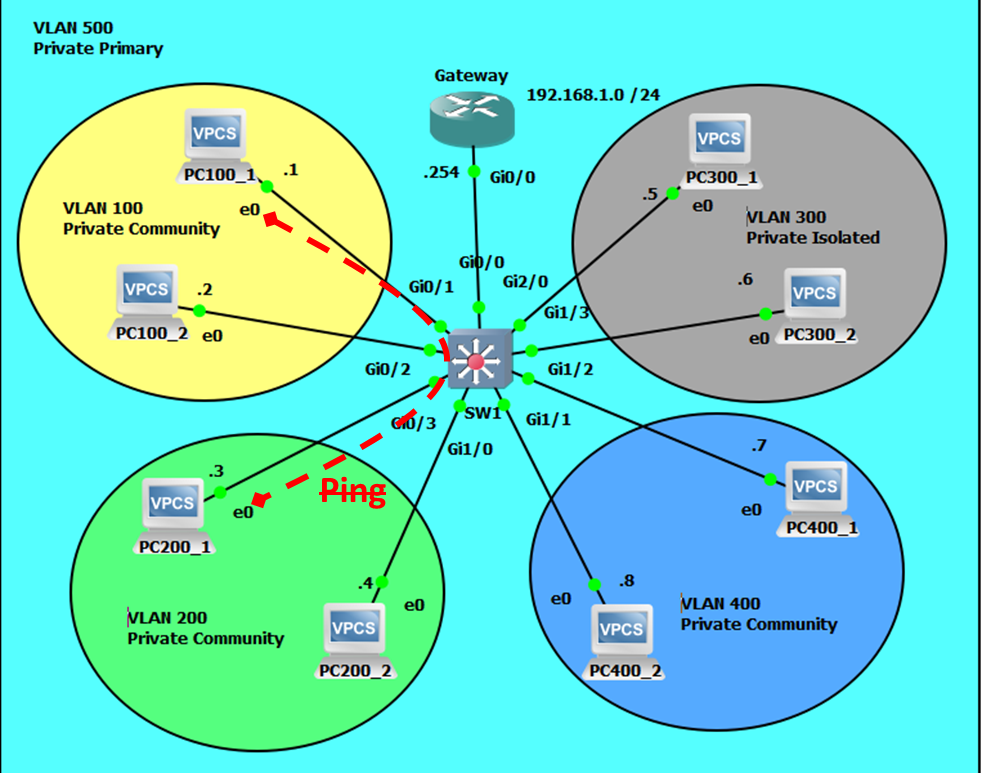
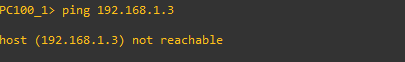
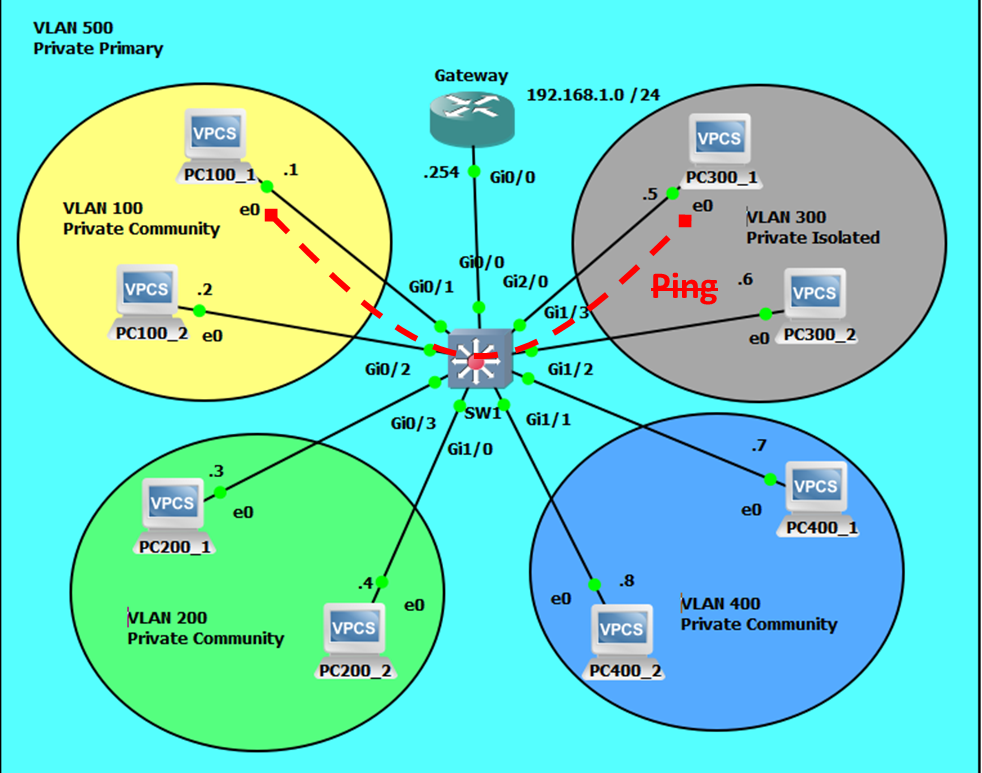
Extra-community VLAN Communication will Fail.
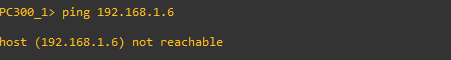
Community-isolated Communications will Fail.
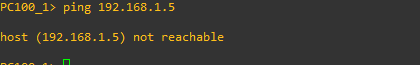
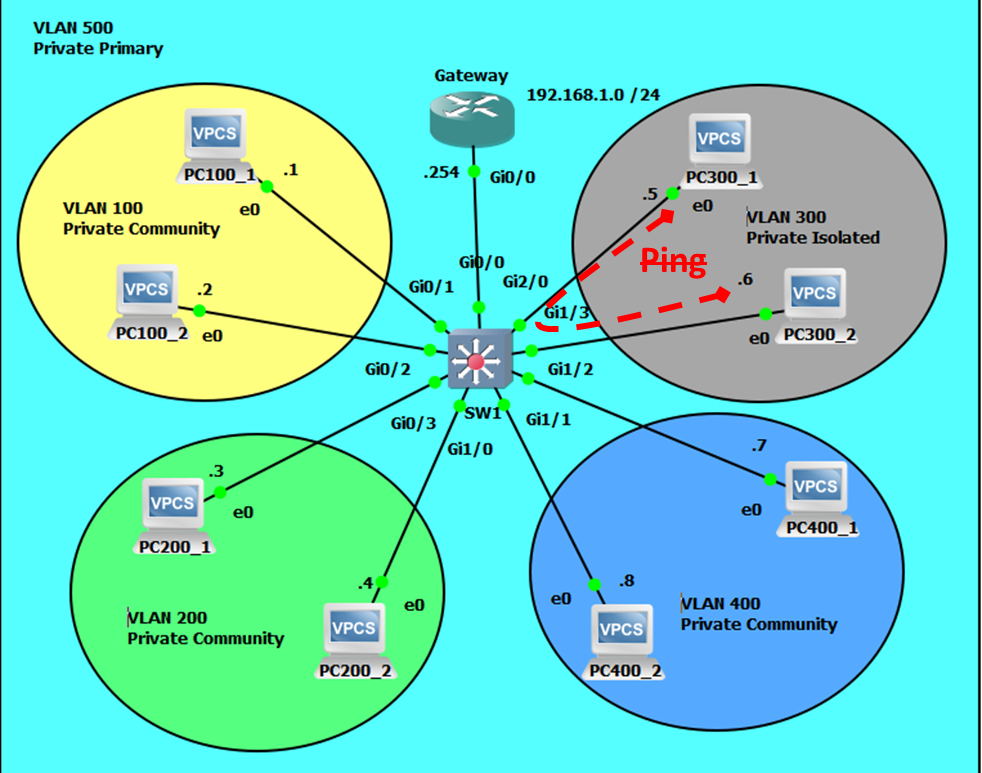
Intra-isolated Communications will Fail.
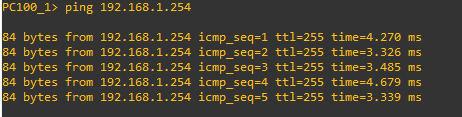
Community-gateway Communicatons will be Successful.
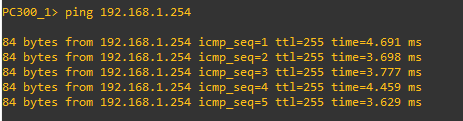
Isolated-gateway Communications will also be Successful.