Cisco Site to Site VPN (Router)
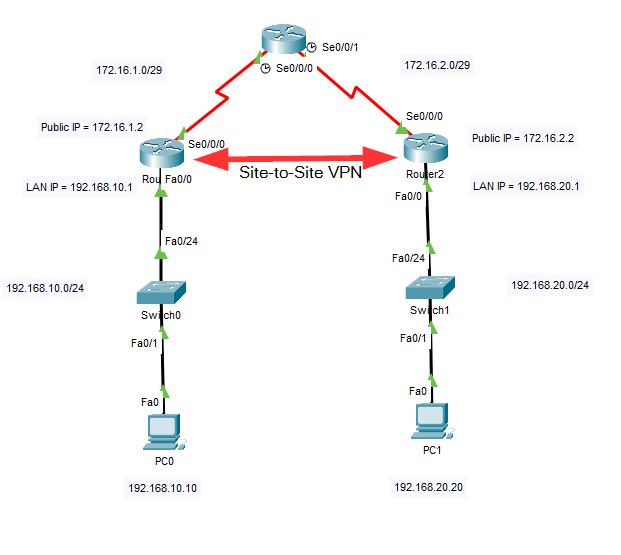
Network Topology
In this network configuration a site-to-site VPN between Router1 and Router2 across the link through Router0.
First let's set up the IP and routing information on all three routers as well as the two PCs.
Router0 IP and Routing Configuration Commands
Router0>enable
Router0#configure terminal
Router0(config)# interface serial 0/0/0
Router0(config-if)#ip address 172.16.1.1 255.255.255.248
Router0(config-if)#no shutdown
Router0(config-if)#interface serial 0/0/1
Router0(config-if)#ip address 172.16.2.1 255.255.255.248
Router0(config-if)#no shutdown
Router0(config-if)#exit
Router0(config)#ip route 192.168.10.0 255.255.255.0 172.16.1.2
Router0(config)#ip route 192.168.20.0 255.255.255.0 172.16.2.2
Router1 IP and Routing Configuration Commands
Router1>enable
Router1#configure terminal
Router1(config)# interface serial 0/0/0
Router1(config-if)#ip address 172.16.1.2 255.255.255.248
Router1(config-if)#no shutdown
Router1(config-if)#interface fastEthernet 0/0
Router1(config-if)#ip address 192.168.10.1 255.255.255.0
Router1(config-if)#no shutdown
Router1(config-if)#exit
Router1(config)#ip route 0.0.0.0 0.0.0.0 172.16.1.1
Router2 IP and Routing Configuration Commands
Router1>enable
Router1#configure terminal
Router1(config)# interface serial 0/0/0
Router1(config-if)#ip address 172.16.2.2 255.255.255.248
Router1(config-if)#no shutdown
Router1(config-if)#interface fastEthernet 0/0
Router1(config-if)#ip address 192.168.20.1 255.255.255.0
Router1(config-if)#no shutdown
Router1(config-if)#exit
Router1(config)#ip route 0.0.0.0 0.0.0.0 172.16.2.1
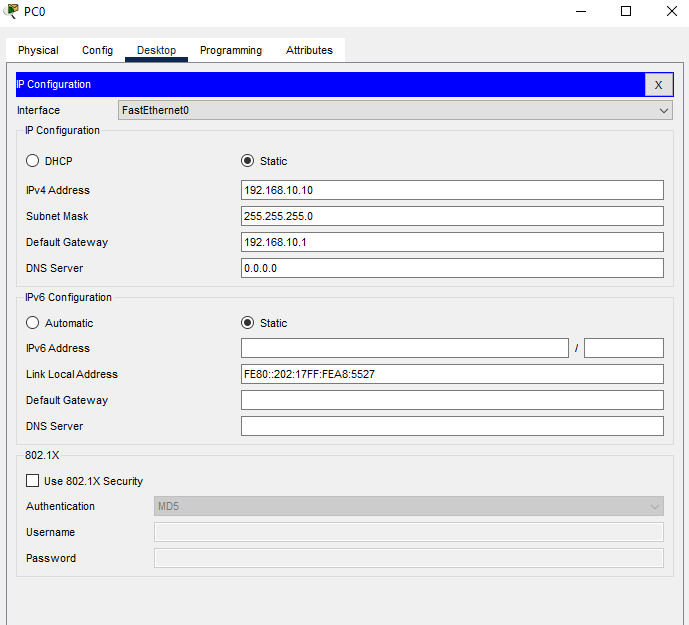
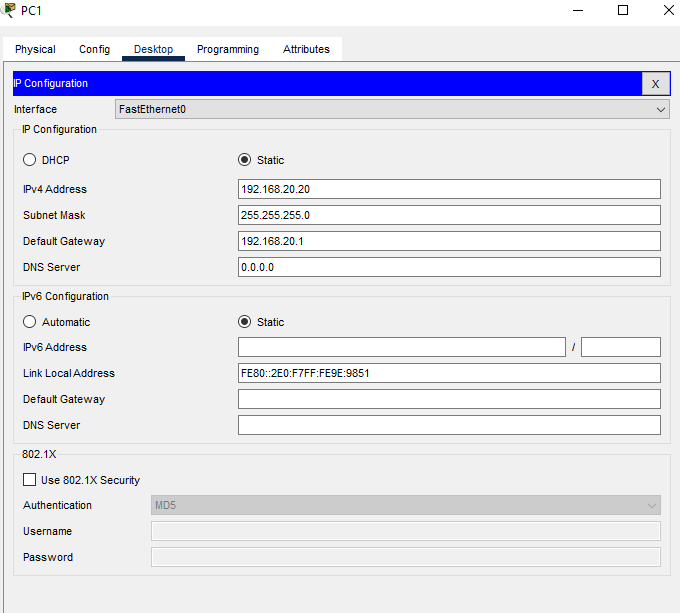
PC Computers IP Configuration
Now that all the routers and PCs have their IP addressing and routing information configured it is time to move on the the specific configuration for enabling the Site-to-Site VPN. This process can be divided into four phases.
Phase 1 - The Key Exchange Setup
| Phase 1 Commands | Notes |
| crypto isakmp enable | |
| crypto isakmp policy 10 | The number can be any number between 1 and 10,000. It identifies the priority of the policy. |
| encryption aes | this could be 3des but aes is more robust. |
| hash sha | sha = secure hash algorithm. md5 could be used but sha is more robust. |
| group 1 | Specifies the Diffie-Hellman group identifier, which the two IPsec peers use to derive a shared secret without transmitting it to each other. Group 1 is 768-bit |
| lifetime 3600 | Specifies the Security Association (SA) lifetime. The default is 86,400 seconds or 24 hours. As a general rule, a shorter lifetime provides more secure ISAKMP negotiations (up to a point). However, with shorter lifetimes, the security appliance sets up future IPsec SAs more quickly. |
| authentication pre-share | |
| crypto isakmp key ciscokey123 address 192.168.1.12 | The italicized text is just a text string that has to match on both sides of the connection. The IP address is the public IP address of our peer on the other side of the VPN connection. |
Phase 2 - Encrypting the Tunnel
| Phase 2 Commands | Notes |
| crypto ipsec transform-set vpnset esp-aes esp-sha-hmac | The italicized text is the set name and can be changed. This could be esp-3des and esp-md5-hmac |
| crypto map vpnset 10 ipsec-isakmp | The number is any number between 1 and 65,535 that identifies the sequence to insert into the crypto map. |
| set transform-set vpnset | |
| match address 100 | Match the addresses in the access control list coming up. This will identify the inside-to-inside traffic flow. |
| set peer 192.168.1.12 | This is the other router's outside interface. |
Phase 3 - Applying the Crypto Map to the Outside Router Interface
| Phase 3 Commands | Notes |
| int s0/0/0 | Whatever the outside interface of the router is (f0/0, g0/2, etc.) |
| crypto map vpnset |
Phase 4 - Creating an Access List to Identify the Traffic Flow (inside to inside LAN traffic)
| Phase 4 Commands | Notes |
| access-list 100 permit ip 192.168.101.0 0.0.0.255 192.168.102.0 0.0.0.255 | These are the inside addresses of both routers. |
Let's start with Router1
Router1 VPN Configuration Commands
Router1>enable
Router1#configure terminal
Router1(config)#crypto isakmp enable
Router1(config)#crypto isakmp policy 10
Router1(config-isakmp)#encryption aes
Router1(config-isakmp)#